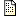OpenSSH 5.9p1 + 7.6p1
syslog-ng 3.3.4 + 3.13.2
Hello, having an Ubuntu server with sftpd running where /var/data/chroot/ is an NFS mount from a remote central NFS server,
and each sftpd user's chroot home is /var/data/chroot/<username>/
and every user has a log device /var/data/chroot/<username>/dev/log which I read in successfully with syslog-ng:
source s_chroot_<username> { unix-stream("/var/data/chroot/<username>/dev/log" optional(yes) ); };
destination d_sftp_<username> { file("/var/log/sftp/<username>.log"); };
log { source(s_chroot_<username>); destination(d_sftp_<username>); };
Now I have a second sftpd server in parallel, with the same user database and also mounts /var/data/chroot/ via NFS, and has the same syslog-ng config,
so every user can login on the one server or on the other. This is for high availability. This works so far.
What is not working now is the sftpd logging: The sftp user's log is only available on one sftp server exclusively, and that is the one where syslog-ng was started least,
because as I understand it takes the exclusive unix socket file lock for each user's /dev/log.
So, if a user logs in on the first server, where syslog-ng was started least, the user's sftp activity is logged on the first server.
But if the user logs in on the second server, it's sftp activity is not logged, neither on the second nor on the first server.
If the syslog-ng is then restarted on the second server, the sftp user's activity is exclusively logged only on the second server and only for logins on the second server.
How can I get the sftp user's activity be logged on each sftp server, when a user logs in to that server, while the user's home is shared on both servers via NFS?
Thanks
Crossposting (because unanswered)
https://unix.stackexchange.com/questions/666641/howto-log-multiple-sftpd-servers-activity-which-users-chrooted-home-is-on-shar
_______________________________________________
openssh-unix-dev mailing list
openssh-unix-dev@mindrot.org
https://lists.mindrot.org/mailman/listinfo/openssh-unix-dev
syslog-ng 3.3.4 + 3.13.2
Hello, having an Ubuntu server with sftpd running where /var/data/chroot/ is an NFS mount from a remote central NFS server,
and each sftpd user's chroot home is /var/data/chroot/<username>/
and every user has a log device /var/data/chroot/<username>/dev/log which I read in successfully with syslog-ng:
source s_chroot_<username> { unix-stream("/var/data/chroot/<username>/dev/log" optional(yes) ); };
destination d_sftp_<username> { file("/var/log/sftp/<username>.log"); };
log { source(s_chroot_<username>); destination(d_sftp_<username>); };
Now I have a second sftpd server in parallel, with the same user database and also mounts /var/data/chroot/ via NFS, and has the same syslog-ng config,
so every user can login on the one server or on the other. This is for high availability. This works so far.
What is not working now is the sftpd logging: The sftp user's log is only available on one sftp server exclusively, and that is the one where syslog-ng was started least,
because as I understand it takes the exclusive unix socket file lock for each user's /dev/log.
So, if a user logs in on the first server, where syslog-ng was started least, the user's sftp activity is logged on the first server.
But if the user logs in on the second server, it's sftp activity is not logged, neither on the second nor on the first server.
If the syslog-ng is then restarted on the second server, the sftp user's activity is exclusively logged only on the second server and only for logins on the second server.
How can I get the sftp user's activity be logged on each sftp server, when a user logs in to that server, while the user's home is shared on both servers via NFS?
Thanks
Crossposting (because unanswered)
https://unix.stackexchange.com/questions/666641/howto-log-multiple-sftpd-servers-activity-which-users-chrooted-home-is-on-shar
_______________________________________________
openssh-unix-dev mailing list
openssh-unix-dev@mindrot.org
https://lists.mindrot.org/mailman/listinfo/openssh-unix-dev